Introduction
Agile Document Guard (Document Guard ®) software product uses advanced operating system kernel technology, high strength encryption algorithms and flexible easy to use security policies. It efficiently solves the problems of both intentional and unintentional information leaks related to legitimate users inside the enterprise.
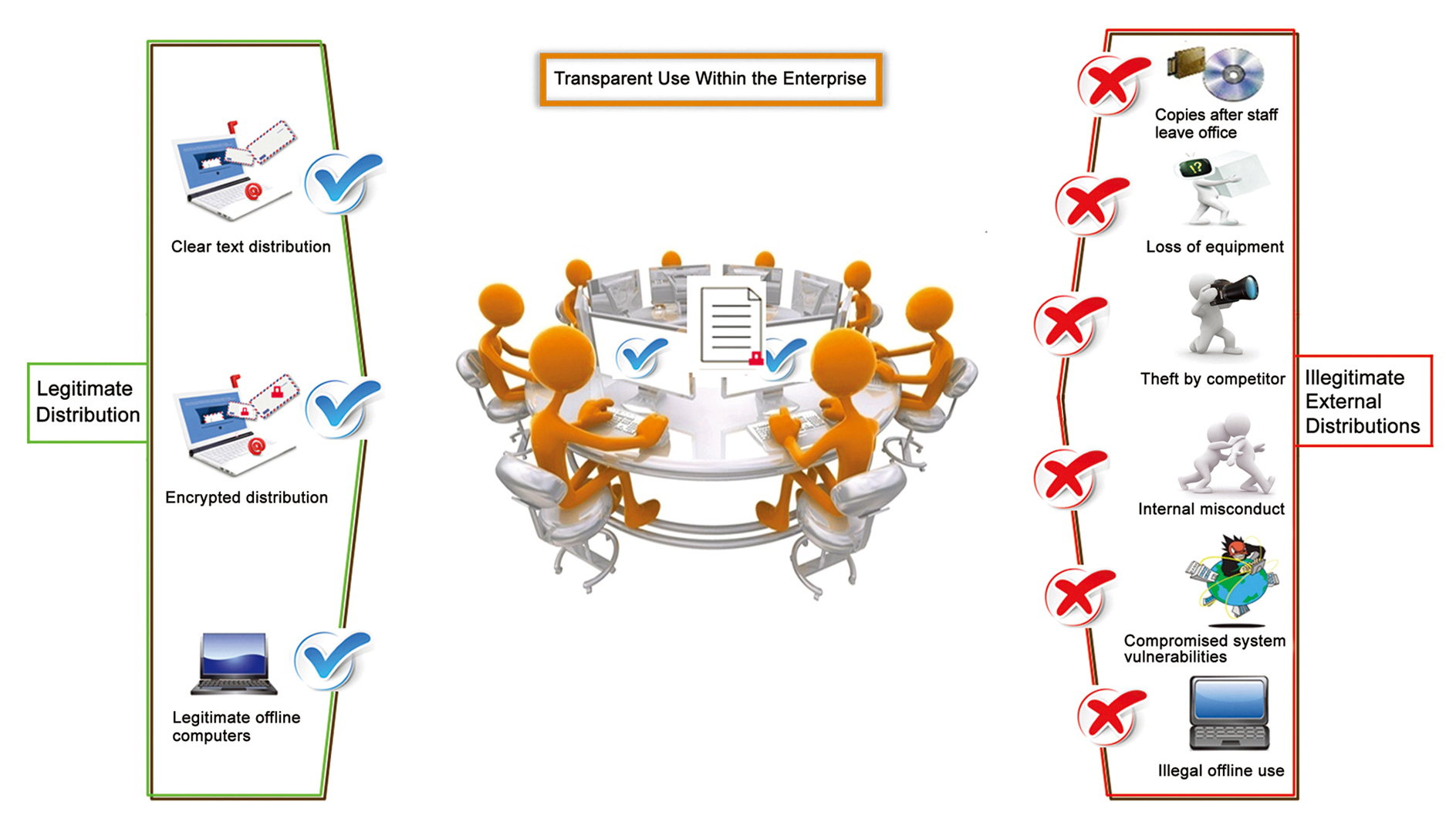
Electronic documents are easy to copy, easy to transmit, and bring convenience and facility to the enterprise. At the same time, the control of electronic documents has always been a difficult problem to solve. Practice shows, that as long as within the system there remain electronic documents without encryption, security systems are not capable to fully stop leakage of secret documents.
DG uses proactive security policies to protect the file during its entire life cycle, from creation to deletion, but it does not change the employee’s normal operating mode and habits. An extraordinary balance has thus been found between security and convenience. DG is in advance of current security systems working on the internal control level, it adds an important supplement. Thanks to the DG encryption of the file at its initial creation, and as the encryption remains transparent during the whole internal enterprise process, a file illicitly transmitted outside of the enterprise can not be opened. As part of a full security system DG’s security function can not be substituted but DG integrates with other security products and makes use of their capabilities so to construct a rigorous complete information security system for the user.
Agile-DG uses a 3-tier architecture composed by DG Server, DG Management Unit and Client Computers. Agile-DG provides the following functions:
Manage the Root Key DG Server: DG Server manages the dongle root key information. A global unique encryption key is generated and distributed to every end node and client computer for file encryption and decryption.Automatic Upgrade Function: Through the DG Server it is possible to introduce the latest Agile-DG upgrade package and with an automatically issued policy it is possible to achieve an automatic upgrade of the Agile-DG environment.
Agile-DG Server Uninstall Code: Installs the DG Client Computer and DG Management Unit’s Uninstall Code. If the authorization code during an eventual un-installation is not correct the DG program will not be unloaded although the installation procedure is executed.
Custom Key: Agile-DG generates an encryption key in addition to the one provided externally. The customer can himself set up this private key, for additional security.
File Decryption: DG Management Unit can decrypt selected files on the Client Computers and generates log records of performed operations.
The Client Computer can be configured to support various kinds of security policies:
Support for different kind of application software running on the Windows platform
Define and apply policies for user offline work mode and associated time period.
Support for stand-alone version of the client
Print operation control policy (can target specific printer models)
Copy screen operation policy
Control policy for copy operations on classified document contents.
Control policy for manipulations of OLE objects inserted in classified documents
Control policy for FTP operations on classified files
Display policy for encrypted file icons on the client computer
Agile-DG provides security level management: Users with high Security Level can open documents made by users with lower Security Level, but users with lower Security Levels can not open High Security level users’ classified files.
AD Domain Integration: This function access information (users, computers, organization structures) in Active Directory’s Domain structure so management information provided to the AD Domain can be used also by Agile-DG. Thanks to the AD Domain Integration function DG Management Unit can apply different policies towards Client Computers.
Organization Management: Agile-DG can based on the actual business organization differentiate users and computers, map corresponding management staff and assign relevant management rights.
Access to Role Management: Login accounts can be provided different rights on the management unit. Management rights include: decrypt files, register client computers, role management access, define policy templates, manage similar users, manage subordinate users, manage subordinate organizations and associated log and audit rights.
Policy Templates: Agile-DG provides a rich set of security policies, though policy templates. These policy templates can be combined and customized. Defined and validated policy templates can be applied for direct use on department level. Computers or users within the department will then automatically inherit the policy strategy defined by the template.
Audit Log: Agile-DG Audit Log function can use every type of log journal and combine collected tracks. With the Audit Log you can move up to earlier events to anticipate and avoid future disasters. It is also possible to analyze and detect the root cause for security incidents.
Fact Sheet
Execution Environment Compatibility
Server/Management Unit:
OS requirement: Windows 2003/R2, 2008/R8,2012
SW Environment:Internet Explorer 6.0 or above,Windows Installer 3.1,IIS 6.0 Service SQL Server 2005 or above
HW requirements (minimum): CPU Dual-core Pentium or above; Memory>512MB; Hard Disk>100MB free space; Network Card>10M/100M; Database (Professional Version): SQL Server 2000/2005
Client Computer:
OS compatibility: Windows 2000 series, XP series, 2003 series, Vista series, 7 series, 8 series,Android,Linux.
HW requirements (minimum): CPU Pentium 4 or above; Memory>512MB; Hard Disk>100MB free space; Network Card >10/100M.
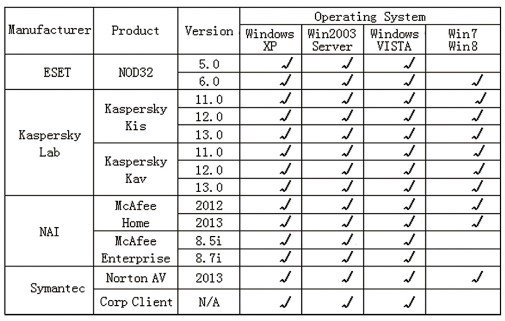
Antivirus Software Compatibility